Google developers have released version 112 of the Chrome web browser. In it they close 16 security gaps. The company classifies some of these as high-risk.
And Google short descriptions only about externally reported vulnerabilities, the threat classifications are not known for all closed vulnerabilities. From the information available, it can be deduced that Google’s developers classify two of the vulnerabilities as high risk. Nine pose a medium threat, while the developers only see a low risk in three others.
Google Chrome vulnerabilities: Attackers could execute code
The two high-risk vulnerabilities are known to be a heap-based buffer overflow in the renderer process (CVE-2023-1810, no CVSS yet, risk “hoch“). The other high-risk vulnerability is based on a use-after-free vulnerability in the frames component of the browser, through which an already freed resource is reused and therefore undefined content can be executed (CVE-2023-1811 , no CVSS yet, hoch).
According to their CVE entries, both vulnerabilities could potentially be exploited by attackers with carefully crafted websites to execute foisted code. Google has accordingly paid the discoverers a reward of 5,000 US dollars and 3,000 US dollars respectively as part of the bug bounty program.
The current versions 112.0.5615.47/.48 for Android, 112.0.5615.46 for iOS, 112.0.5615.49 for Linux and Mac and 112.0.5615.49/50 for Windows fix the vulnerabilities. Google distributes them automatically over the coming days. However, due to the risk posed by the vulnerabilities, Chrome users should check promptly whether they are using the current version.
Google Chrome: current version active?
To check whether the web browser is already up to date, it is sufficient to call up the settings menu via the symbol with the three stacked dots to the right of the address bar and the path “Help” – “About Google Chrome”.
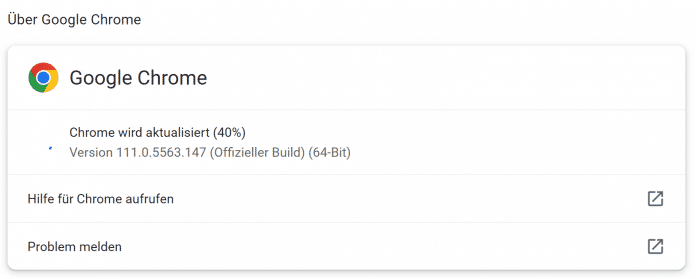
The current status of Chrome is displayed in the settings menu under “Help”-“About Google Chrome”. If an update is available, the call triggers the update process and, if necessary, prompts you to restart the browser.
(Bild: Screenshot/dmk)
If necessary, calling up the version dialog triggers the update process and prompts you to restart the browser. Linux users usually have to launch the distribution’s own software manager to check for and install updated packages.
The gaps also affect the underlying Chromium project. The web browsers based on it, such as Microsoft’s Edge, should therefore also be equipped with the security updates shortly. Google’s developers don’t seem to be running out of work: around two weeks ago, they had already fixed eight vulnerabilities in Google Chrome.
See also:
(dmk)
